Difference between revisions of "Auditable events and tamper-resistance (MU3)"
From OpenEMR Project Wiki
Bradymiller (talk | contribs) |
Bradymiller (talk | contribs) |
||
| Line 11: | Line 11: | ||
:(d)(2)(i)(C) | :(d)(2)(i)(C) | ||
::*End-user device encryption is always on per (d)(7), so not applicable. | ::*End-user device encryption is always on per (d)(7), so not applicable. | ||
:(d)(ii) | :(d)(2)(ii) | ||
::*All logging needs to be on by default. | ::*All logging needs to be on by default. | ||
:(d)(iii) | :(d)(2)(iii) | ||
::*Logging can only be disabled by a limited set of users. | ::*Logging can only be disabled by a limited set of users. | ||
:(d)(vi) | :(d)(2))(vi) | ||
::*Need to detect manipulation of log. | ::*Need to detect manipulation of log. | ||
Revision as of 03:19, 14 October 2020
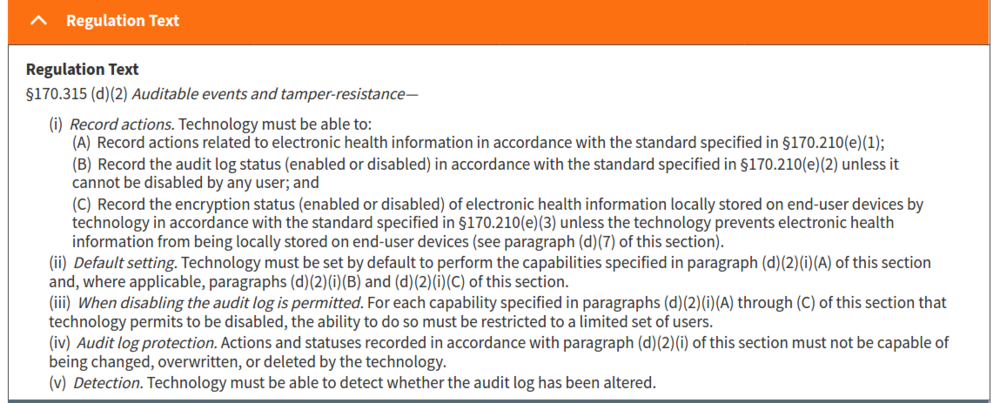
Issues:
- (d)(2)(i)(A)
- The audit log must record the information specified in sections 7.1.1 through 7.1.3 and 7.1.6 through 7.1.9 of the standard specified in ASTM E2147-18 and changes to user privileges when health IT is in use.
- TODO
- Analyze 7.1.1 through 7.1.3 and 7.1.6 through 7.1.9 of the standard specified in ASTM E2147-18
- Record changes in user privileges (to fully support this, added logging for when change a user's access control group)
- (d)(2)(i)(B)
- The audit log must record the information specified in sections 7.2 and 7.4 of the standard specified in ASTM E2147-18 when the audit log status is changed. Interestingly, 7.2 and 7.4 do not exist in ASTM E2147-18, but in a prior ASTM E2147 version used in MU2, 7.2 was 'Date and Time of Event' and 7.4 was 'User Identification' (reference https://healthcaresecprivacy.blogspot.com/2012/09/meaningful-use-stage-2-audit-logging.html).
- (d)(2)(i)(C)
- End-user device encryption is always on per (d)(7), so not applicable.
- (d)(2)(ii)
- All logging needs to be on by default.
- (d)(2)(iii)
- Logging can only be disabled by a limited set of users.
- (d)(2))(vi)
- Need to detect manipulation of log.
Final:
- To ensure accurate time, server will need to set up a Network Time Protocol server that supports version 4 Network Time Protocol (NTP) as defined by RFC 5905.
Progress:
- ASTM E2147-18 7.1.1 through 7.1.3 and 7.1.6 through 7.1.9, 7.2 and 7.4
- Any changes to a user’s privileges must be captured to meet this criterion (e.g., user account creation, user switches roles and new privileges are assigned, revoking privileges, account disabling, etc.).